Published
Shaping an Infrastructure Security Area in the North Atlantic
Subjects: European Union North-America
Introduction
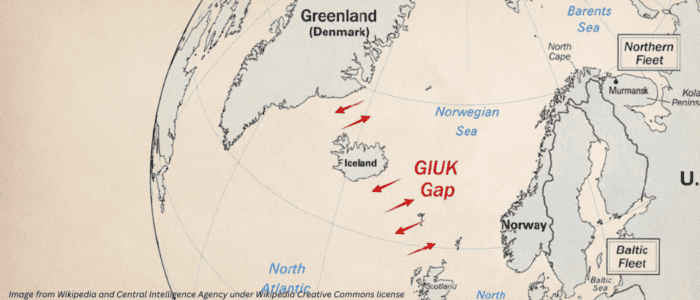
The North Atlantic quadrant encompasses the United States, Canada, Greenland, Iceland, the United Kingdom, and the Nordic Peninsula. At its centre lies the Greenland–Iceland–United Kingdom (GUIK) gap, arguably the most important maritime choke point in the Western Hemisphere. It serves as the Arctic transit route between East and West acts as a containment zone Russian Navy’s Northern Fleet. This continuum of allied nations extends into the Baltic Sea, where the narrow passages of the Gulf of Finland and the Øresund Strait form the first and second lines of defence against Russia’s Baltic Fleet based in Kaliningrad and St Petersburg.
NATO and allied forces have long monitored this maritime corridor for signs of adversarial submarine or surface fleet movements, deployed underwater sensors, and coordinated intelligence-sharing efforts in response to recent incidents targeting undersea infrastructure near Svalbard, Shetland and Faeroe islands, and the Baltic countries.
These incidents have prompted an urgent reassessment of infrastructure security in the region, underlining the shared responsibility for safeguarding critical physical links that connect North Atlantic allies from Newport, Rhode Island, to Estonia’s eastern border with Russia at Narva. A single break in a submarine cable or a large-scale disruption in terrestrial infrastructure could cut off financial transactions and government communications across the continuum.
Crucially, these partners already share responsibility for the physical security of critical digital assets. NATO allies in the Arctic collaborate in patrolling, monitoring, and protecting these infrastructure corridors, ensuring that a breach in one area does not compromise the security of another.
A Full-Spectrum Challenge
The modern digital ecosystem in the North Atlantic relies on several overlapping infrastructure domains, each with its own vulnerabilities and security requirements. Submarine cables carry approximately 95 per cent of transoceanic data traffic, forming the backbone of international communication. However, their vast geographic footprint, spanning thousands of kilometres along the ocean floor, leaves them susceptible to interception, tampering or physical damage by state and non-state actors.
Another critical layer is the deployment of 5G networks, which have rapidly become indispensable as the infrastructure that underpins all other critical infrastructure—from medical services and transport to energy grids. Unless fully trusted, these networks introduce national security and supply chain risks that could be exploited by adversarial entities.
Internet Exchange Points (IXPs) also play a crucial role by serving as the physical intersections where internet service providers hand over data traffic to each other. While IXPs optimise connectivity and reduce latency, they are hotspots for electronic surveillance or sabotage if not adequately secured.
Finally, Low Earth Orbit (LEO) satellites represent an emerging frontier in global broadband coverage, offering connectivity even in remote areas like the Arctic. LEO satellite constellations are particularly useful for communications in the region, where remote stretches of ocean, rugged coastlines, and extreme latitudes can make terrestrial and geostationary (GEO) satellite coverage less reliable. These satellite systems, however, share similar concerns about potential signal interception, jamming, and other intentional interference.
Safeguarding these interconnected infrastructure domains across land, sea, air, and space demands robust coordination, interoperability and investments.
Omni-modal Trans-European Networks
Concerns over submarine cable security have intensified following high-profile sabotage incidents. In recent months, the Government of France has acquired Nokia’s loss-making submarine cable division (originally the French Alcatel Submarine Network), leaving NEC of Japan as the only remaining private alternative among French, Chinese, and US state-controlled providers.
Within the EU, the upcoming Council of EU telecom ministers is expected to express comprehensive support for submarine cable infrastructure, rapid incident response, and robust deterrence as necessary for resilient connectivity. Some EU member states, particularly the Nordic and Baltic states, have called for expanding the Trans-European Network (TEN) programme to include digital infrastructure alongside its existing energy and transport priorities. This would unlock funding pathways, expedite regulatory processes, and reinforce the EU’s trusted connectivity concept.
In parallel, Denmark, Sweden, Estonia, Latvia, and Lithuania are among the few EU countries that have taken executive or legislative decisions to use European vendors in their 5G deployment. Chinese state-backed vendors have failed to gain a foothold in fixed and mobile infrastructure in Greenland, which remains self-governing under the Danish Constitution. In Norway, all major operators have opted for European vendors, while Finland’s national regulatory agency, Traficom, recently announced it will review its stance on high-risk vendors. Meanwhile, Ireland is one of the countries that the European Commission deems to have failed to comprehensively implement the EU 5G Toolbox.
In effect, the United States, Canada, Greenland, the UK, the Nordics, and the Baltics form a corridor of trusted 5G network deployment spanning a significant portion of the Northern Hemisphere. Ireland, Iceland, and Finland remain notable outliers, though they may tighten their regulatory frameworks to align with their neighbours. Poland is also set to enact stricter measures, leveraging its role as the EU’s rotating presidency to unify EU 5G security approaches.
A “Claustra Borealia”
This EU-level strategy aligns a non-NATO country (Ireland) into a common security architecture via the EU regulatory acquis on telecoms. Conversely, non-EU countries (the UK, Norway, and Iceland) align with the same framework via the NATO, ensuring a consistent defence posture.
A better-integrated and defended transatlantic digital infrastructure—a Claustra Borealia—must be capable of swiftly rerouting and mitigating localised disruptions to safeguard broader connectivity. From the start, NATO and the EU’s combined and overlapping structures surpass the mechanisms within the Quad. The defence and policy alignment in the north would also exert diplomatic pressure on Continental Europe, where some remain reluctant to expand maritime security or supplier scrutiny.
However, the EU-NATO cooperation remains fragmented by institutional factors. The EU leads crisis management and hybrid threats, while NATO is dedicated to mutual defence. No formal agreement exists between the two on addressing a combined digital infrastructure threat, often without attribution. Sensor deployments and continuous remote monitoring of infrastructural nodes are costly and likely to involve EU funds. Response plans and rapid-action task forces must combine various capabilities, including undersea operations and cyber forensics that involve both organisations.
Besides the lack of real-time intelligence sharing and CSIRT capabilities in both organisations, NATO intelligence, EU cybersecurity agencies, telcos, the coast guard, and port authorities must collaborate to jointly identify and respond to threats that might target cables, networks, IXPs, data centres, and satellite ground stations. Rightly or wrongly, some national efforts are under question, as evidenced by recent points made by the new US administration that may be traced back to the Joint Arctic Command over Greenland.
Final thoughts
In conclusion, today’s telegeography and its challenges cannot be tackled in isolation through national telecom laws or a single governance forum, and an attack in any communication domain must trigger an integrated cross-institutional response to deter adversaries.
The Canadian G7 Presidency is naturally placed to initiate discussions on digital infrastructure security. The EU and NATO must also expand their cooperation: Russia’s invasion of Ukraine has brought the two institutions closer, culminating in the 2022 Joint Declaration that reinforced commitments to closer cooperation on hybrid warfare and cyber defence.
Digital infrastructure security sits in the middle of a Venn diagram formed by EU funding and technical initiatives (including the NIS Cooperation Group) on one side, and NATO’s Cooperative Cyber Defence Centre and the First Standing Maritime Group (SNMG1) on the other. Shared responsibility between the two can establish common standards for trusted interoperability and ensure a continuum without a weakest link.
So much in this great article, I read it just after I had read Gideon Rachman’s piece on ‘Vance’s Real Warning to Europe’ in today’s FT. He talked of forming a European Mutual Defence Pact outside of Nato that extends beyond EU members, I thought how that would fit in the middle of the Venn Diagram you describe. Time for Europe and North Atlantic to collaborate on domestic innovation in digital infrastructure security given new geopolitical alignments. And time to make sure it’s our own low earth satellites that we use, which would be good for economy as well as increased security.